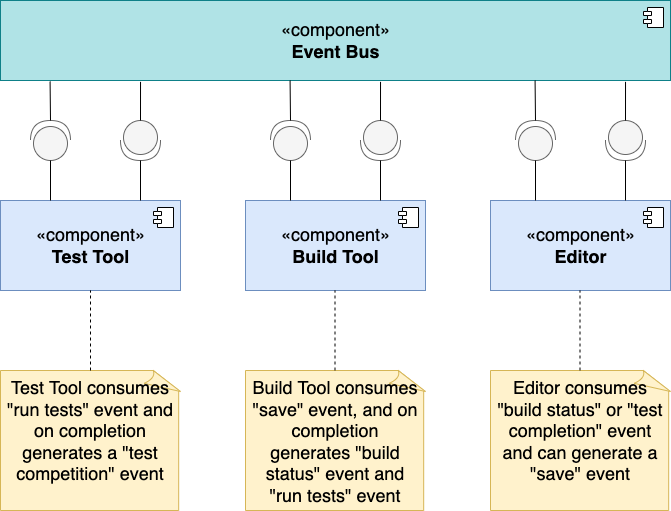
In this architectural style, the fundamental elements in the system are events. Events can be signals, user inputs, messages, or a data from other functions or programs. Events act as both indicators of change in the system and as triggers to functions. In this paradigm, functions take the form of event generators and event consumers. Event generators send events and event consumers receive and process these events. A function can be both an event generator and an event consumer. Event consumers are called implicitly based on event sent from event generators.
Event-based functions experience implicit invocation. The defining feature of implicit invocation is that functions are not in direct communication with each other. All communication between them is mediated by an event bus. We can think of the event bus as the connector between of all event generators and consumers in the system.
To achieve this structure, we first bind an event and an event consumer via the event bus. That is, each event consumer registers with the event bus to be notified of certain events. When the event bus detects an event, it distributes the event to all appropriate event consumers. When the event bus detects an event, it distributes the event to all appropriate event consumers. The observer design pattern manifests the event-based architectural style.
One way to implement the event bus is to structure the system to have a main loop that continually listens for events. When an event is detected, the loop calls all the functions bound to that event.
Continue reading “Event based architectural style” →